Risk management according to NIS2
16.03.2025
In this article, we will show how to manage risks in the Configuration Database CMDB according to NIS2 (EU Directive No. 2022/2055 on measures for a high common level of cybersecurity across the Union), or the upcoming amendment to the Czech Cybersecurity Act, which transposes the NIS2 Directive into Czech legislation. According to it, regulated service providers are, among other things, obliged to manage assets and manage risks.
Failure to comply with the requirements of the amendment to the Act carries a number of sanctions. The NIS 2 Directive stipulates that for breach of the obligations arising from Articles 21 to 23 of this Directive, fines with a maximum sanction of at least EUR 10 million or 2% of global turnover for so-called “essential entities”, or EUR 7 million or 1.4% of global turnover for so-called “important entities” should be imposed. These categories correspond to providers of regulated services in the regime of higher and lower obligations under the amendment to the Act, and the above-mentioned sanctions are also reflected in the Act in Section 59, paragraph 4. Asset and risk management falls under the requirements, non-compliance with which is thus sanctioned by the Act.
Other sanctions may include, for example, a temporary ban on the exercise of the function of a member of the statutory body if the provider has repeatedly failed to meet the obligation to eliminate the identified deficiencies, until the deficiencies are eliminated.
Of course, there is also a reputational risk.
With regard to asset management, the provider is obliged, pursuant to Section 9, paragraph 2:
a. to determine its primary assets
b. to assess whether these primary assets are related to the provision of a regulated service
c. to determine the supporting assets for primary assets pursuant to letter b)
As stated in the explanatory memorandum to the amendment to the law, mapping primary assets and keeping proper records is a key requirement for the correct implementation of the requirements of the NIS 2 directive.
The
Configuration Database CMDB will provide us with asset registration and capture of the link to the regulated services provided and supporting assets. Risk management then needs to be linked to the CMDB in order to be able to capture the propagation of risks through the various supporting assets they may relate to, to the regulated services.
For any Configuration Item (CI), we can record the risks that relate to it, similar to how we record risks, for example, for a project.
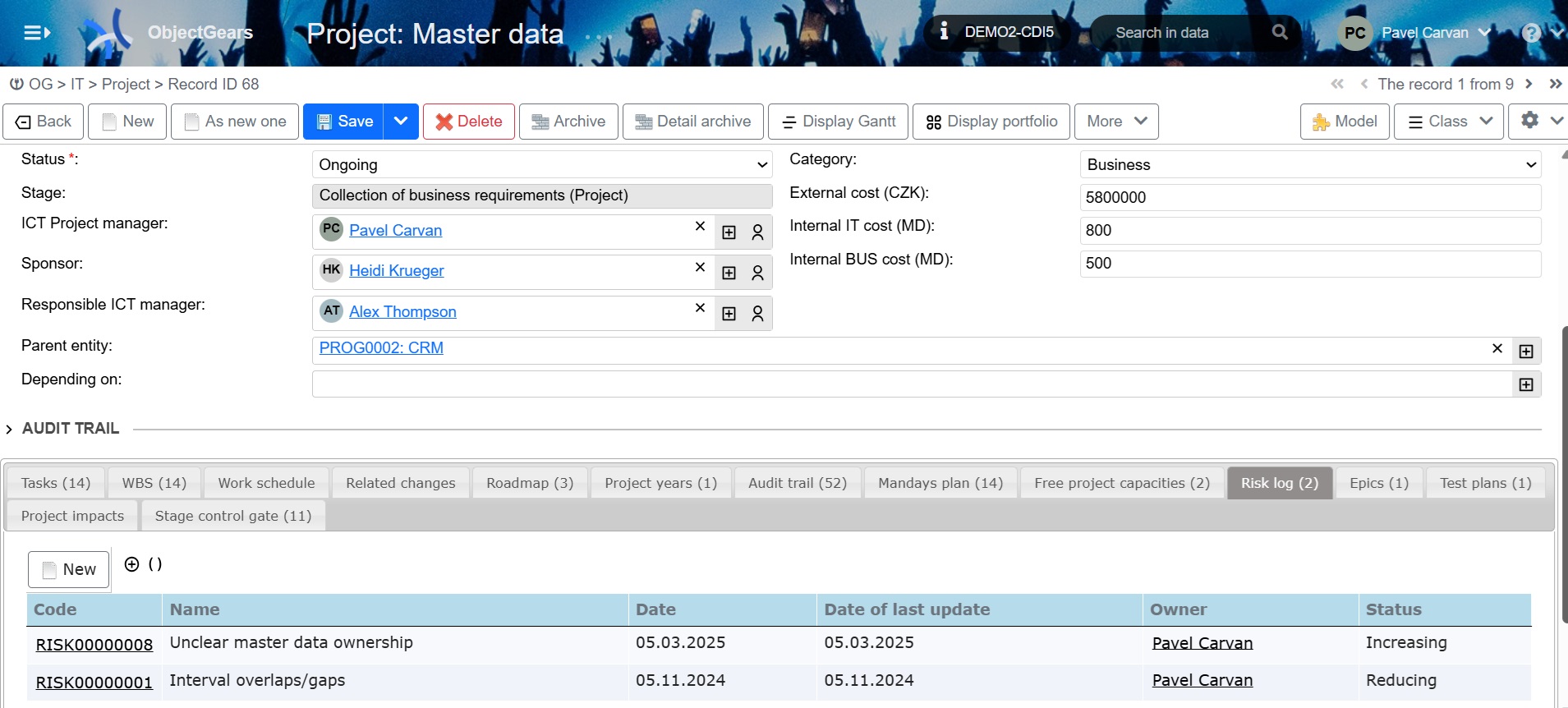
Figure 1 – Project card with two risks on the Risk log tab (in the bottom part of the picture)
Most of us have probably already encountered project risk recording. Similarly, we can record risks in the Configuration Item or, for example, in the supplier record, as required by NIS2.
Let's show this again with an example. If you have a "no name" component in your infrastructure, there is a risk of an unknown supplier associated with it. It's not just that you don't have support for the component from the supplier, but you are using a product that you cannot trust, like a reputable manufacturer from a democratic state, not to have installed, for example, a so-called backdoor in the device that would allow to take control of the device or otherwise abuse it.
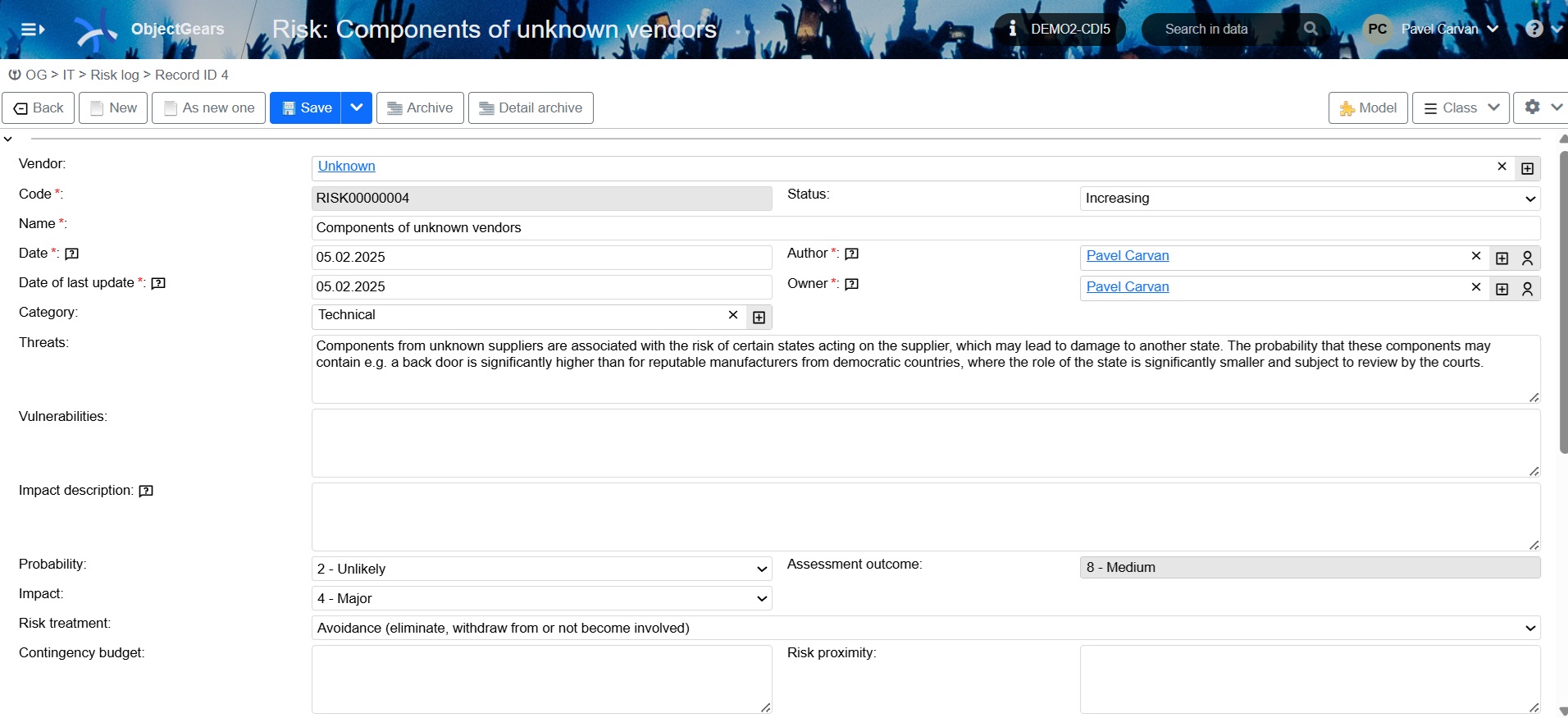
Figure 2: Risk associated with an unknown supplier
We do not have to tie the risk to a specific Configuration Item, but we can register it with a hypothetical "unknown" supplier as in the image above, so that it is propagated to all Configuration Items that have this Unknown supplier listed.
If we have already registered a risk, we can simply connect it to other Configuration Items. We will use this in a relatively frequent case when the given risk does not concern only one specific Configuration Item, but, for example, all network elements of a given model that suffer from a certain vulnerability or are at risk of maintenance expiration.
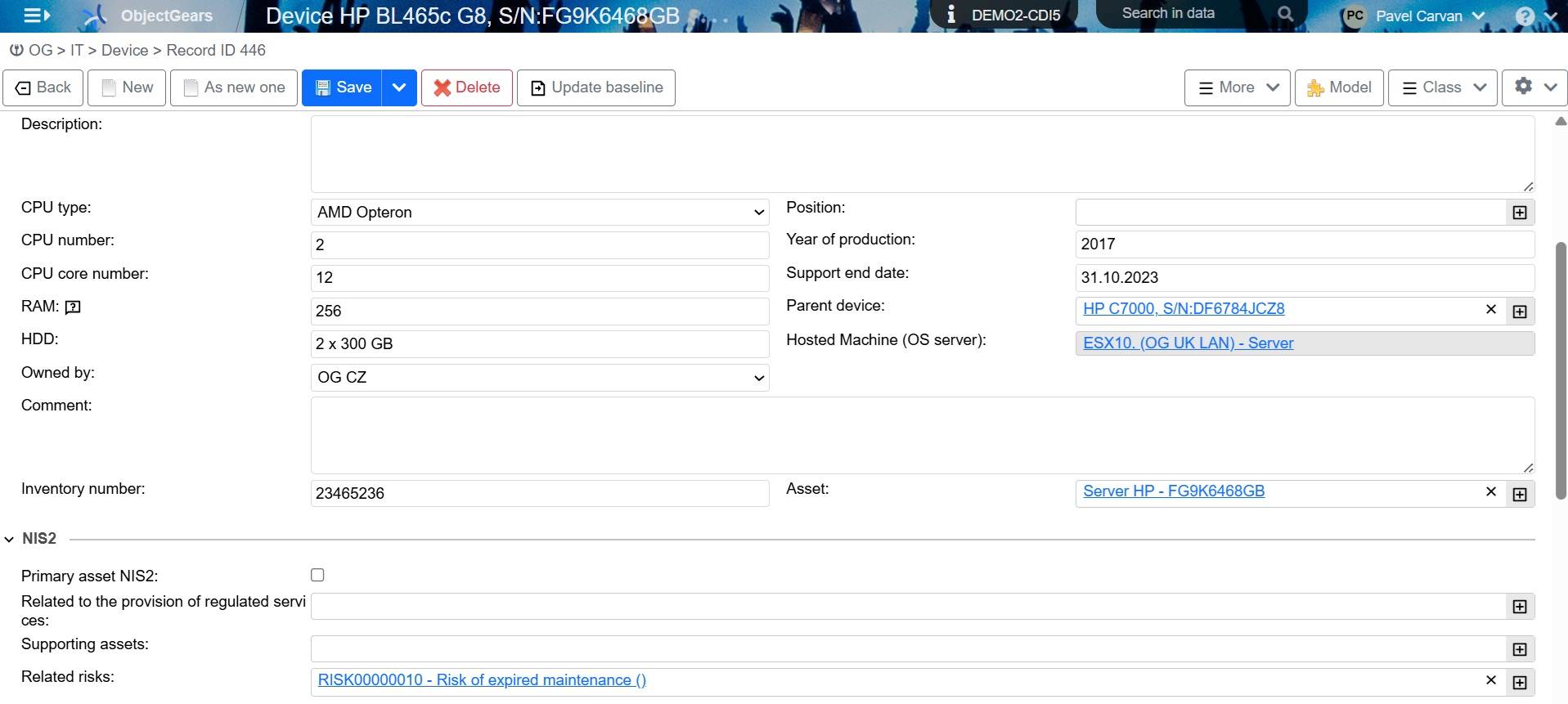
Figure 3: Additional related risks that are already registered can be linked to the Configuration Item (see section NIS2 in the figure below)
We have recorded the risks and now we need to show how they are reflected in the primary assets associated with the provision of regulated services.
There are two ways to link assets to regulated services. Either we will use the supporting assets records for each configuration item and the connection to the regulated services provided, as shown in the image below, or we will track the connection through the specific connections of individual types of configuration items.
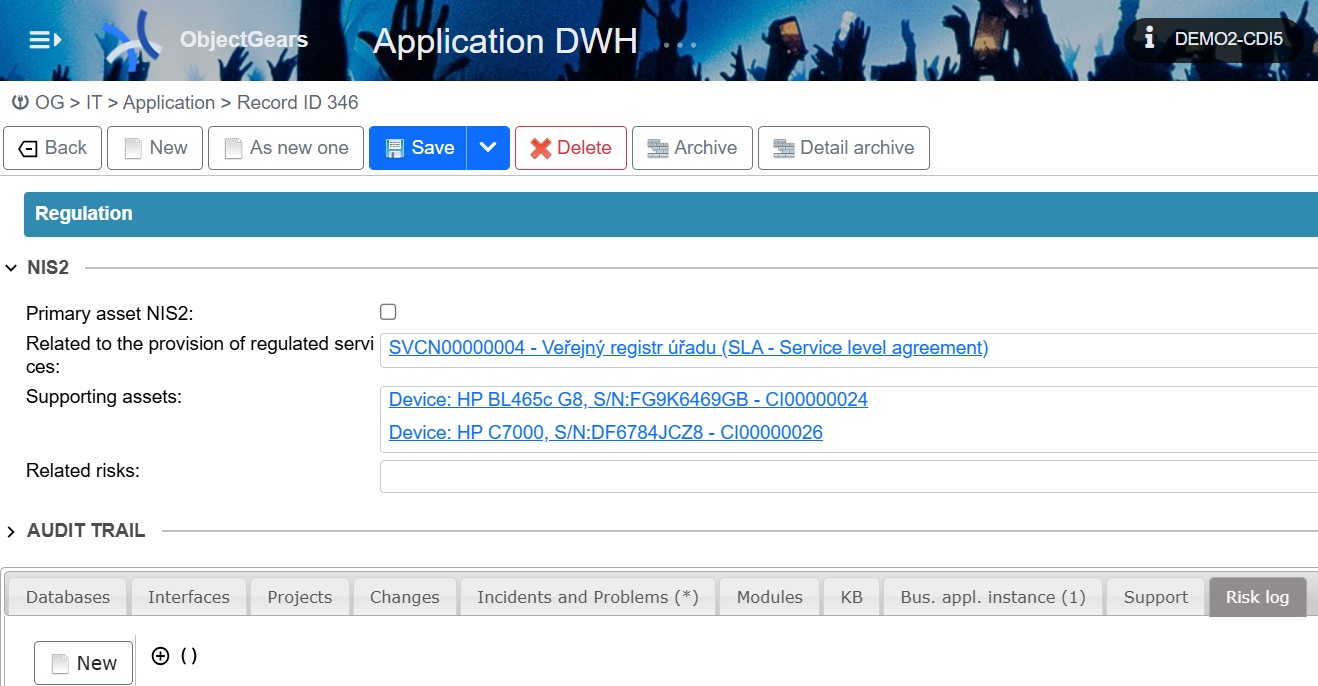
Figure 4: We can add related regulated services and supporting assets to the Configuration Item in the Regulation/NIS2 section
The first method is simpler, but it means duplicating the records of relationships that already result from the links recorded in the configuration database and that are displayed in the diagrams.
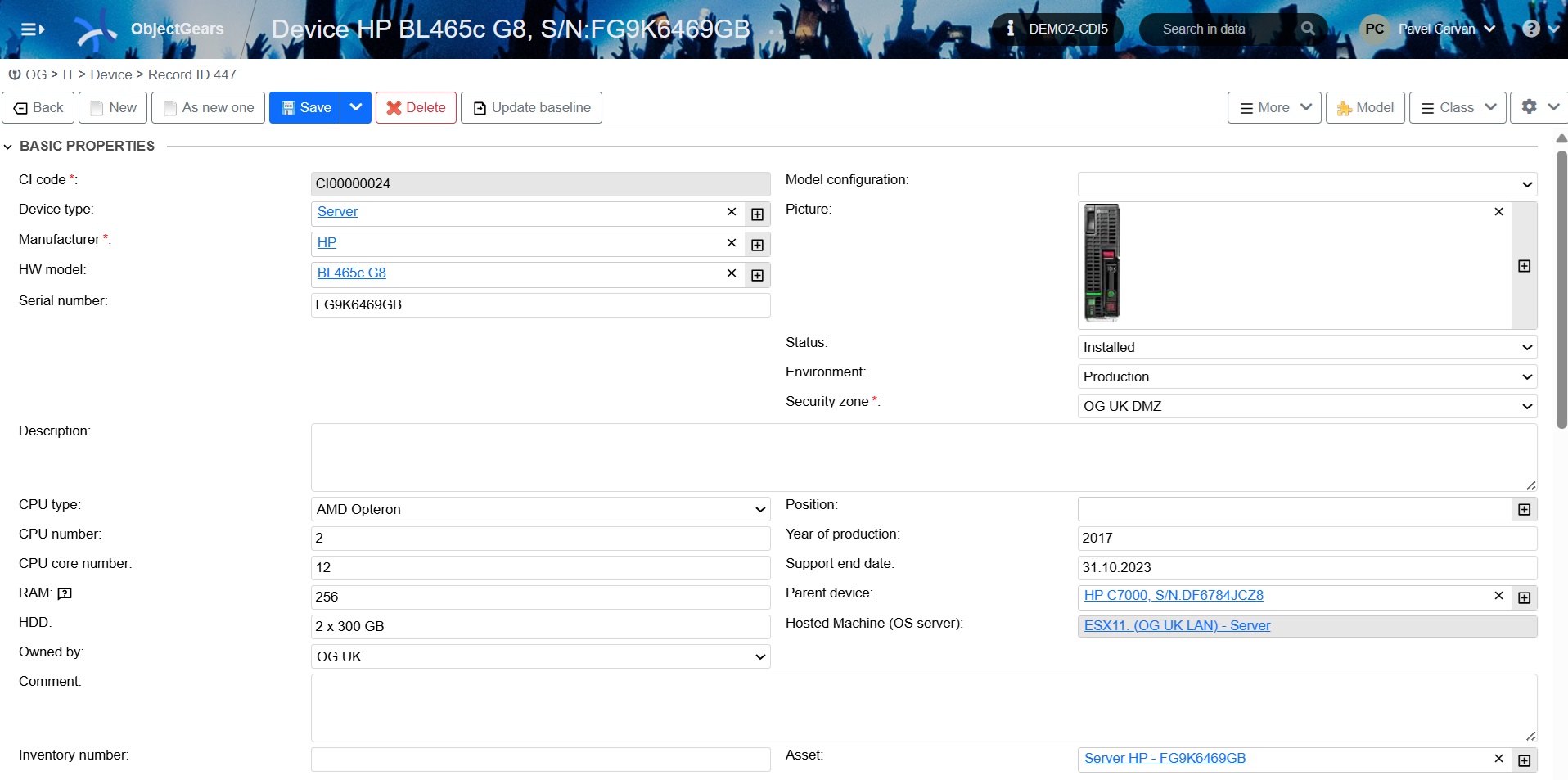
Figure 5: Configuration item (device/hardware server) with links to other configuration items (see links in blue)
Configuration items are linked to each other according to the model we use in the configuration database. There may be several other configuration items between the hardware affected by the risk and the regulated service that implement the link.
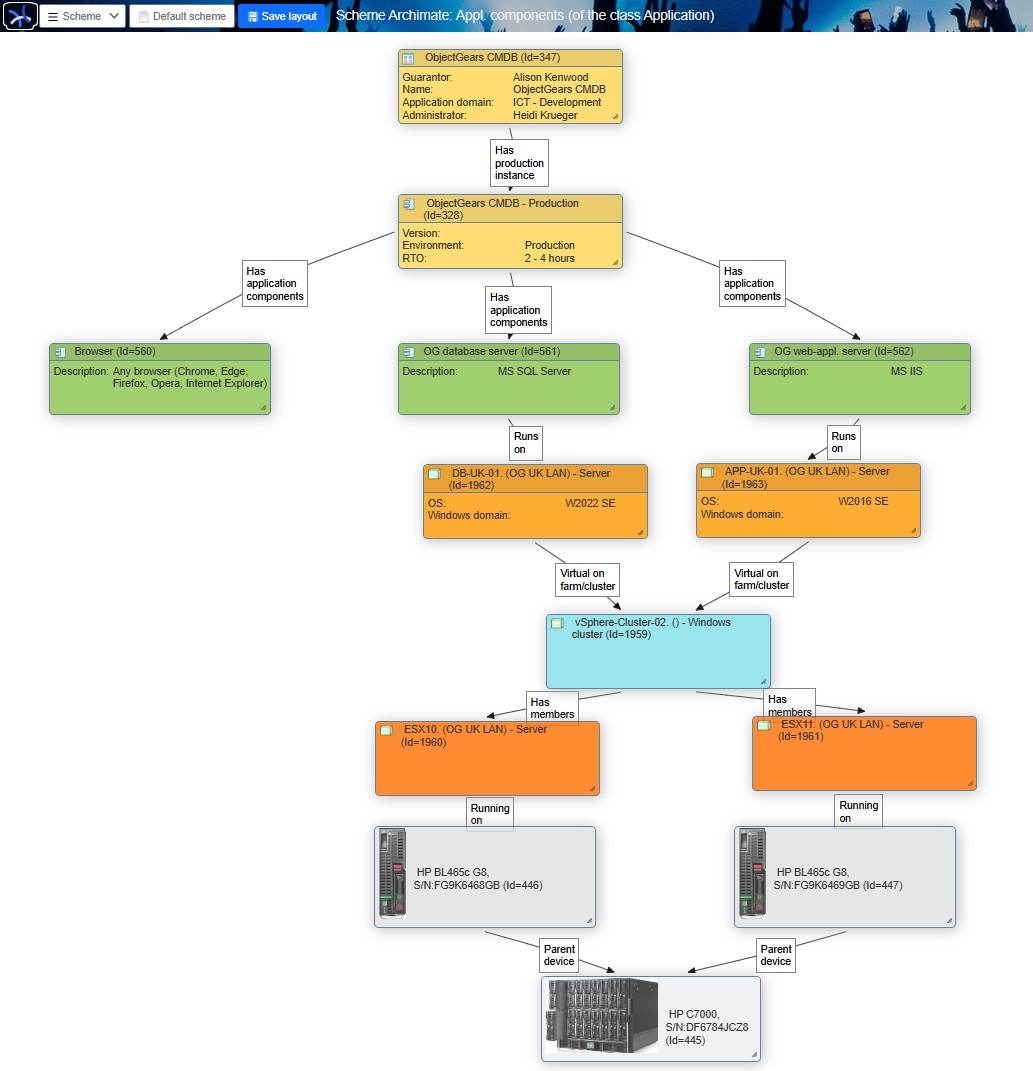
Figure 6: Diagram depicting the relationships of configuration items from hardware, through servers forming a virtualization cluster, to application components and the application.
We can then find the relationship of the risk to primary assets and regulated services for each risk.
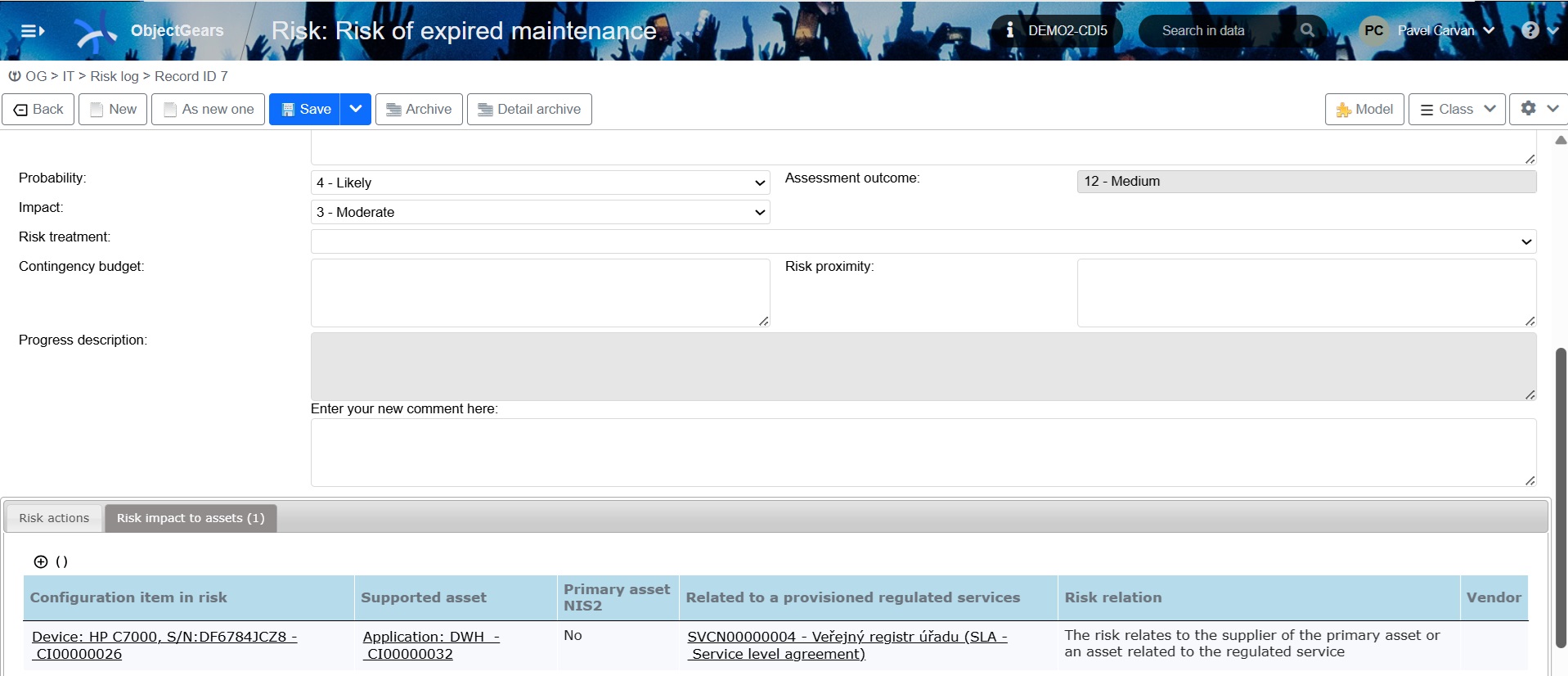
Figure 7: At the bottom of the risk card, we see the impact on configuration items, the assets they support, and the regulated services.
Take a look at the impact to the CMDB reference model.
Learn more about Cyber security and legislation requirements.